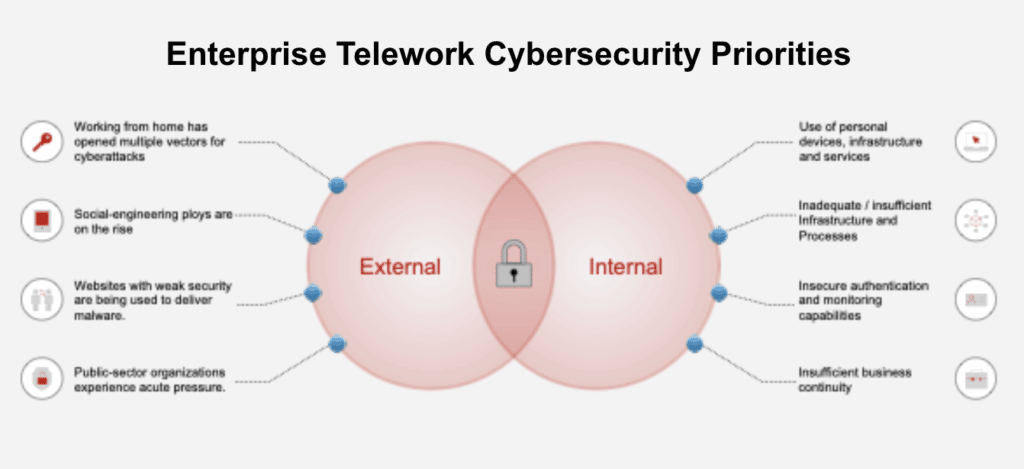
In the evolving landscape of modern labor practices, a profound shift is underway, reshaping traditional notions of employment and digital safeguards. This section delves into the intricate interplay between the transformation of job environments and the critical need for robust digital protection measures. As we navigate this new terrain, understanding the implications for individual autonomy and digital integrity becomes paramount.
Telecommuting, once a niche arrangement, has surged in prominence, challenging conventional frameworks of oversight and confidentiality. The advent of remote collaboration tools has not only expanded geographical boundaries but also introduced new complexities in maintaining the sanctity of sensitive data. Employers and employees alike face the dual challenge of enhancing productivity while safeguarding against breaches of digital privacy.
Moreover, the surveillance of employee activities in these remote settings raises significant ethical and practical questions. Balancing the need for operational efficiency with respect for individual privacy is a delicate task. This article explores the emerging protocols and technologies aimed at establishing a harmonious equilibrium between these often conflicting priorities.
As we advance, the integration of sophisticated cyber defense mechanisms is inevitable. The stakes are high, with the potential for significant repercussions in the event of lapses in digital security. This discussion aims to illuminate the strategies and safeguards necessary to protect both the enterprise and the individual in this brave new world of work.
The Evolution of Remote Work
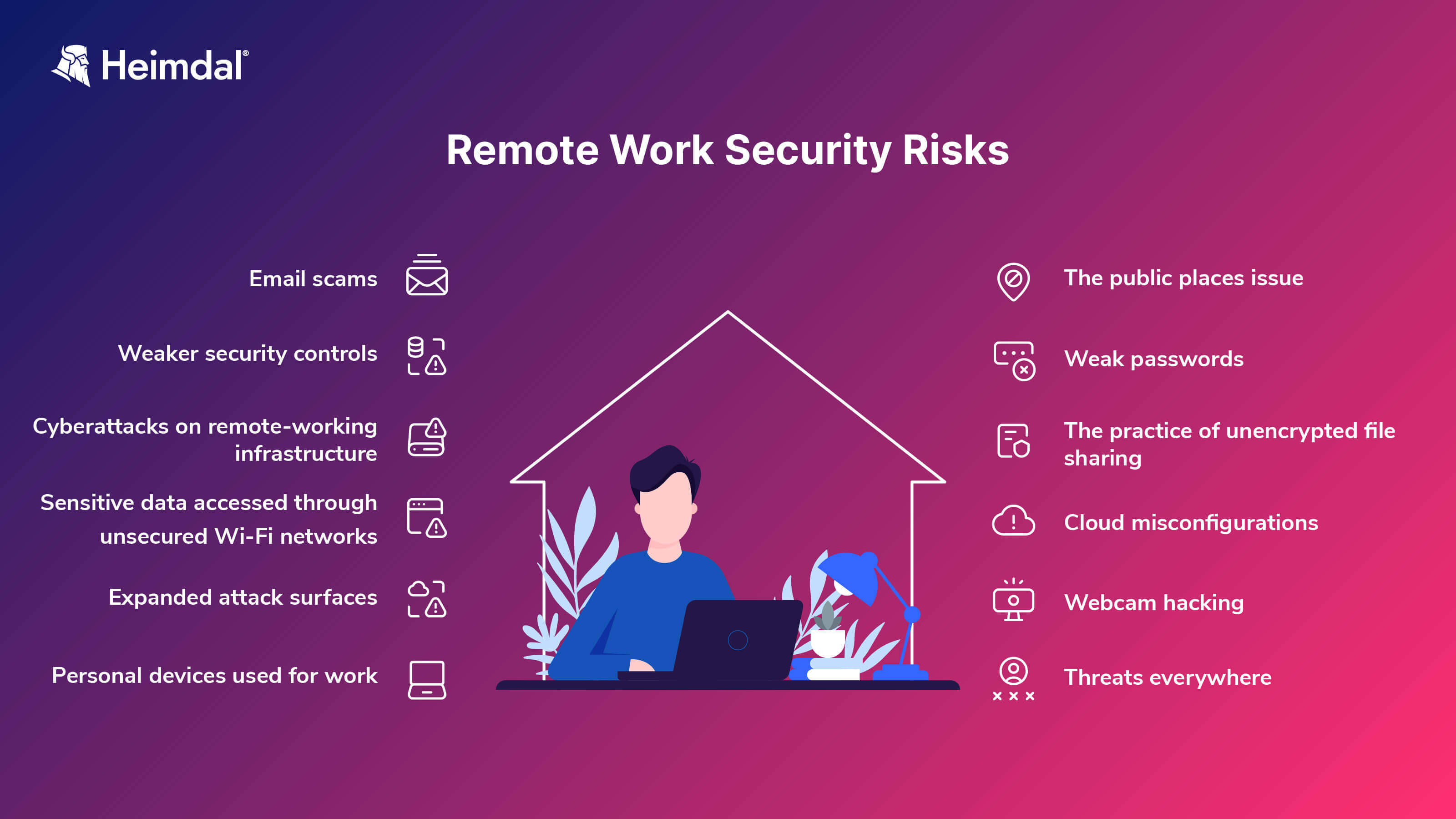
Over the past few decades, the concept of conducting tasks from locations outside traditional office settings has undergone significant transformation. Initially viewed as a niche arrangement, it has now become a mainstream practice, influencing various aspects of professional life.
The shift towards this mode of operation was gradual, initially spurred by advancements in communication technology. The ability to connect and collaborate virtually has been pivotal in expanding the scope of where and how work is performed. This evolution has not only changed the physical landscape of workplaces but also necessitated new approaches to management and employee engagement.
As organizations worldwide embrace this trend, the dynamics of the workplace are being redefined. Factors such as flexibility, autonomy, and the integration of work and personal life are becoming central to discussions about employee satisfaction and productivity. Moreover, the cultural shift towards valuing outcomes over presence has led to a reevaluation of traditional performance metrics.
This section delves into the profound impact of telecommuting on the structure and functioning of modern workplaces. It explores how the transition to remote setups has necessitated changes in leadership styles, team coordination, and the overall organizational culture. The discussion also covers the challenges and opportunities that arise from this evolving work paradigm, highlighting the need for innovative strategies to maintain efficiency and morale in a distributed workforce.
Impact of Telecommuting on Workplace Dynamics
In recent times, the shift towards working from home has significantly altered the traditional office environment. This section delves into how these changes affect the interactions and structures within professional settings, emphasizing the implications for both employees and management.
Communication Patterns: One of the most profound impacts of remote setups is on communication. Virtual meetings and digital correspondence have replaced face-to-face interactions, influencing the speed and quality of information exchange. This shift necessitates new strategies for maintaining effective dialogue and ensuring clarity in directives.
Collaboration and Teamwork: Remote work environments challenge the traditional dynamics of collaboration. Teams must adapt to digital tools for project management and brainstorming, which can either enhance or hinder creativity and productivity depending on their effectiveness and the team’s familiarity with them.
Leadership and Supervision: The role of leaders and supervisors has evolved in remote settings. They must now manage teams from a distance, focusing on outcomes rather than presence. This requires a shift in leadership styles, emphasizing trust and autonomy while still maintaining oversight and support.
Work-Life Balance: The blending of home and work life can have both positive and negative effects on employee well-being. While some appreciate the flexibility, others may struggle with boundaries, leading to potential burnout. Organizations must consider policies that promote a healthy balance, ensuring that remote work is sustainable in the long term.
In conclusion, the transformation of workplace dynamics due to remote work is complex and multifaceted. It requires a nuanced understanding and continuous adaptation to ensure that both the organization’s goals and the well-being of its employees are met.
Data Privacy in the Digital Age
In this section, we delve into the intricate dynamics of safeguarding sensitive details in an era dominated by digital technologies. As our interactions and transactions increasingly migrate online, the need to protect our private data becomes paramount.
The proliferation of digital platforms has led to a surge in the collection and analysis of user data. This has significant implications for individual autonomy and security. Companies and governments are constantly developing new methods to gather and utilize this information, often without the explicit consent or knowledge of the individuals involved.
One of the major concerns is the potential misuse of collected data. Without stringent regulations and oversight, personal details can be exploited for commercial gain, political manipulation, or even identity theft. It is crucial, therefore, to establish robust frameworks that ensure data is used ethically and responsibly.
Moreover, the digital age has introduced complex challenges in terms of data protection. Cyber threats are becoming increasingly sophisticated, necessitating advanced security measures. From encryption technologies to multi-factor authentication, various tools are being employed to fortify data defenses. However, the rapid evolution of cyber threats means that these measures must be continually updated and improved.
In conclusion, the digital revolution has transformed the landscape of personal data protection. It demands a vigilant and proactive approach from both individuals and organizations to safeguard sensitive information against the myriad risks present in the digital realm.
Challenges of Protecting Personal Information Online
In the current digital landscape, safeguarding sensitive details from unauthorized access is a paramount concern. This section delves into the complexities of maintaining confidentiality in an environment where data breaches are increasingly common.
The proliferation of digital platforms and the reliance on internet-based services have heightened the risk of unauthorized access to confidential details. Hackers and malicious entities continuously devise new strategies to exploit vulnerabilities in online systems, making it crucial for individuals and organizations to implement robust protective measures.
One of the primary challenges is the diversity of threats that exist. From phishing scams to sophisticated malware, the methods used to compromise security are varied and ever-evolving. This necessitates a dynamic approach to defense, where security protocols must be regularly updated and adapted to counter the latest threats.
Additionally, the global nature of the internet complicates regulatory efforts. Different jurisdictions have varying laws and standards regarding data protection, which can create gaps in coverage and enforcement. This international disparity requires a coordinated global response to ensure comprehensive protection across borders.
Furthermore, the integration of personal devices into professional settings adds another layer of complexity. The blurring of lines between personal and professional use of technology can lead to lapses in security, as personal devices may not adhere to the same rigorous security standards as corporate ones. This necessitates clear policies and training to ensure that all devices used for work purposes meet necessary security requirements.
In conclusion, the protection of sensitive details online is fraught with challenges that require ongoing attention and adaptation. By understanding these challenges and implementing effective strategies, individuals and organizations can better safeguard their valuable information against the myriad of threats present in the digital world.
Cybersecurity Measures for Remote Employees
In this section, we delve into the critical strategies that organizations must adopt to safeguard their digital assets and personnel operating outside traditional office settings. Ensuring robust protection mechanisms is essential in the current landscape where digital threats are ever-evolving.
Secure Access Protocols: One of the foundational steps in enhancing security for offsite staff is the implementation of stringent access controls. This includes the use of multi-factor authentication (MFA) which requires users to provide two or more verification factors to gain access to a resource such as an application, online account, or a VPN.
Encrypted Communication Channels: To protect sensitive data in transit, it is imperative to use encrypted communication tools. This ensures that even if data is intercepted, it remains unreadable without the decryption key. Tools like Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are crucial for maintaining the integrity and confidentiality of data.
Regular Security Training: Equipping employees with the knowledge to identify and avoid potential security threats is vital. Regular training sessions should cover topics such as phishing awareness, safe internet practices, and the importance of maintaining strong, unique passwords for different accounts.
Endpoint Protection: With employees using various devices to connect to company networks, it is essential to have robust endpoint protection in place. This includes antivirus software, firewalls, and intrusion detection systems that can monitor and protect each device from malware and unauthorized access.
Regular Updates and Patch Management: Keeping all systems and software up-to-date is crucial in mitigating vulnerabilities that could be exploited by cybercriminals. Automated patch management tools can help ensure that all devices are updated promptly with the latest security enhancements.
Secure Data Storage and Backup: Implementing secure cloud storage solutions and regular data backups can prevent data loss in the event of a security breach or system failure. It is also important to ensure that these backups are encrypted and stored in geographically diverse locations to enhance resilience.
By integrating these measures, organizations can significantly enhance their defense against cyber threats, ensuring the safety and productivity of their remote workforce.
Implementing Robust Security Protocols
This section delves into the critical measures necessary to fortify the safety of digital interactions within a distributed workforce. It explores the multifaceted approach required to ensure that sensitive exchanges are safeguarded against potential threats, emphasizing the importance of comprehensive strategies that encompass both technological and procedural elements.
As organizations adapt to a more dispersed operational model, the implementation of stringent security protocols becomes paramount. These protocols are designed to protect against unauthorized access and data breaches, ensuring that all transactions and communications are secure. Below is a table summarizing key components of robust security protocols:
| Component | Description | Importance |
|---|---|---|
| Encryption | The process of converting data into a code to prevent unauthorized access. | Essential for securing sensitive information during transmission. |
| Two-Factor Authentication (2FA) | An additional layer of security requiring users to provide two different authentication factors to verify their identity. | Significantly reduces the risk of unauthorized access. |
| Regular Updates | The practice of regularly updating software and systems to patch vulnerabilities. | Prevents exploitation of known weaknesses by malicious actors. |
| Firewalls | Security systems that monitor and control incoming and outgoing network traffic based on predetermined security rules. | Acts as a barrier between secure internal networks and untrusted external networks. |
| Security Training | Educating employees about potential threats and best practices for maintaining security. | Empowers employees to identify and mitigate security risks. |
Implementing these protocols not only enhances the security posture of an organization but also instills confidence among employees and stakeholders. It is crucial for organizations to continuously evaluate and refine their security measures to adapt to evolving threats and technological advancements.
Employee Monitoring: Ethical Considerations

In this section, we delve into the complex interplay between enhancing operational efficiency and safeguarding individual liberties within the professional environment. As organizations increasingly adopt strategies to track employee activities, it becomes crucial to examine the ethical dimensions of such practices.
Balancing Productivity and Individual Privacy is a multifaceted challenge that requires a nuanced approach. On one hand, businesses are driven to optimize performance and ensure compliance with standards. On the other, there is a growing recognition of the need to respect the privacy rights of employees. This balance is not merely a legal requirement but a moral imperative that reflects the values of a respectful and inclusive workplace.
The implementation of surveillance technologies can lead to significant improvements in productivity, but it also raises questions about the extent to which an individual’s personal space is encroached upon during working hours. Transparency and consent are key elements in this discussion. Employers must clearly communicate the reasons for monitoring, the specific data collected, and how it is used. Moreover, obtaining explicit agreement from employees regarding these practices is essential to maintain trust and ethical integrity.
Furthermore, it is important to consider the psychological impact of constant monitoring. While it may deter misconduct and boost output, it can also create a stressful environment, potentially leading to decreased morale and increased turnover. Therefore, organizations must be mindful of the psychological well-being of their staff and implement monitoring in a way that respects their dignity and autonomy.
In conclusion, while the drive for efficiency is understandable, it should not overshadow the fundamental rights of employees. A thoughtful and ethical approach to monitoring can lead to a more harmonious and productive workplace, where the dignity of each individual is upheld alongside organizational goals.
Balancing Productivity and Individual Privacy

In this section, we delve into the intricate dance between enhancing operational efficiency and safeguarding personal liberties. As organizations strive to optimize performance, they must also navigate the complex landscape of respecting individual rights and maintaining ethical standards.
Legislation and Data Protection play pivotal roles in this balancing act. Laws are continually evolving to address the challenges posed by the digital era, aiming to protect users while not stifling innovation or productivity. These regulations are designed to ensure that while businesses collect and analyze data to improve their services, they do so without infringing on the privacy of their users.
Global Regulations Shaping Privacy Norms have become increasingly stringent and comprehensive. They reflect a global consensus on the importance of privacy and the need for robust frameworks to protect it. These regulations not only dictate how data should be handled but also impose significant penalties for non-compliance, thereby incentivizing businesses to adopt best practices in data management.
As we explore the implications of these laws, it becomes clear that they serve as both a constraint and a guide for organizations. They provide a framework within which businesses can innovate and compete, ensuring that the pursuit of productivity does not come at the expense of individual privacy.
In conclusion, the interplay between productivity and privacy is a delicate one, requiring careful navigation by both legislators and businesses. By understanding and adhering to the evolving legal landscape, organizations can foster a culture that values both efficiency and respect for personal data.
Legislation and Data Protection
This section delves into the regulatory frameworks that govern the safeguarding of sensitive details in the digital realm. It explores how various jurisdictions are adapting their legal structures to address the evolving challenges of protecting individual rights in the online space.
As the digital landscape continues to expand, numerous regions have recognized the imperative to fortify their legislative measures. Here, we outline some of the key global regulations that are shaping norms related to the protection of personal data:
- General Data Protection Regulation (GDPR) – Originating from the European Union, this regulation sets stringent standards for the handling of personal data, impacting businesses worldwide.
- California Consumer Privacy Act (CCPA) – Enacted in California, USA, this law enhances privacy rights and consumer protection for residents, setting a precedent for other states.
- Personal Data Protection Act (PDPA) – In Singapore, this act provides a framework for the protection of personal data, emphasizing consent and accountability.
- Brazil’s General Data Protection Law (LGPD) – Similar to GDPR, this Brazilian law aims to harmonize data protection rules across the country, impacting both public and private sectors.
- India’s Personal Data Protection Bill – Although not yet law, this bill proposes a comprehensive framework for data protection, reflecting India’s growing digital economy.
These regulations not only dictate how data should be processed and protected but also impose significant penalties for non-compliance. They underscore the global trend towards stricter data governance, ensuring that organizations worldwide are held accountable for their data handling practices.
Moreover, these laws often require businesses to implement robust security measures, conduct regular audits, and ensure transparency in their data practices. They also empower individuals with rights such as access, correction, and deletion of their data, thereby enhancing control over personal information.
In conclusion, the legislative landscape for data protection is rapidly evolving, driven by the increasing recognition of the importance of safeguarding personal data in the digital age. As new regulations emerge and existing ones are refined, the global approach to data protection continues to mature, reflecting a commitment to privacy and security in the digital world.
Global Regulations Shaping Privacy Norms
This section delves into the pivotal role of international laws in defining and enforcing standards related to user confidentiality. As digital interactions become more pervasive, the need for comprehensive frameworks that safeguard individual rights becomes increasingly critical.
The landscape of global rules governing user confidentiality is diverse and evolving. Various regions have adopted distinct approaches to ensure the protection of sensitive details, reflecting their unique cultural, economic, and political contexts. Below is a table summarizing some of the key regulations from around the world:
| Region | Regulation | Key Features |
|---|---|---|
| Europe | General Data Protection Regulation (GDPR) | Enhanced rights for individuals, strict consent requirements, and significant penalties for non-compliance. |
| California, USA | California Consumer Privacy Act (CCPA) | Provides consumers with the right to know, delete, and opt out whitepages-out of data sales, and imposes fines for violations. |
| Brazil | Lei Geral de Proteção de Dados (LGPD) | Similar to GDPR, it regulates the processing of personal data, aiming to protect individual rights. |
| India | Personal Data Protection Bill | Proposes a framework for the protection of personal data, including restrictions on data localization and stringent penalties. |
These regulations not only set the baseline for what constitutes adequate protection of sensitive details but also influence the development of global standards. As businesses increasingly operate across borders, understanding and complying with these diverse regulations is essential for maintaining ethical and legal integrity.
In conclusion, the global regulatory environment plays a crucial role in shaping norms related to user confidentiality. As technology continues to advance, these regulations will likely evolve, requiring constant vigilance and adaptation from all stakeholders involved in digital interactions.

