In our digital age, personal information circulates more freely than ever before. Companies collect data from various sources to gain insights into consumers’ habits and preferences. This vast ocean of information can lead to both opportunities and dangers. With every click we make online, we leave a trail that can be traced, analyzed, and categorized.
While the advantages of personalized services are undeniable, there lurks a darker side. Vulnerabilities increase when sensitive information falls into the wrong hands. Unscrupulous entities can exploit this data for malicious purposes, leaving unsuspecting individuals at risk of severe consequences. Many are unaware of how pervasive this issue has become.
As technology continues to advance, understanding the implications of information privacy becomes essential. Our digital footprints can sometimes be more revealing than we realize, offering a treasure trove of insights for ill-intentioned actors. Therefore, knowledge about how personal details are aggregated and used is crucial for protecting oneself in an increasingly interconnected world.
Recognizing the intricate web that connects individuals, corporations, and malicious actors is vital for safeguarding personal safety. Awareness is the first step to empowerment. Take charge of your online presence and understand the potential risks involved in sharing personal information. The more informed you are, the better you can defend against potential exploitation.
Overview of Data Brokers

In today’s world, the exchange of personal information has become a lucrative business. Individuals often unknowingly provide valuable insights about themselves. These insights are then compiled, analyzed, and sold. The whole operation is vast, complex, and often hidden from public view. Knowledge and awareness about how this process works can empower consumers.
Many companies engage in the collection and distribution of personal data. This industry thrives on the information that can be gathered from various sources. The sources include social media profiles, online purchases, public records, and even surveys. Every click and interaction contributes to a comprehensive profile.
Understanding how these enterprises operate is essential. They utilize advanced technologies for data gathering. Algorithms play a crucial role in sorting through information. This enables them to generate detailed consumer profiles. Companies may sell insights to marketers, researchers, or even government agencies.
Additionally, the information gathered can be categorized in numerous ways. For instance, demographic details such as age, gender, and location are crucial. Behavioral data reveals purchasing habits and preferences. These segments help businesses target potential customers more effectively. The intricate web of information makes it possible for companies to predict consumer behavior.
- Collection of personal information from various digital footprints.
- Utilization of advanced algorithms for analyzing trends.
- Sale of insights to interested parties, including marketers.
- Creation of detailed profiles based on demographic and behavioral data.
Moreover, the scale at which these companies operate can be staggering. They often gather billions of data points, creating an extensive database filled with intricate details about individuals. This colossal amount of information allows them to discern patterns and behaviors, leading to increasingly personalized marketing strategies.
Overall, the intricate mechanisms behind this industry wield significant influence over consumer experiences. Awareness and knowledge about these practices can be invaluable. Understanding the landscape helps individuals better navigate their online presence. After all, knowledge is power in a world where information reigns supreme.
How Data Brokers Operate
The mechanisms behind personal information aggregation are intricate and multifaceted. Many entities engage in this practice, collecting a wealth of details about individuals. This information can range from basic identifiers to more sensitive data. The ultimate aim? To create comprehensive profiles that can be sold or shared with others. It often feels like an unseen web, constantly gathering insights about daily lives.
These companies utilize various techniques to acquire personal information. Some methods include scraping public records, purchasing data from other organizations, or even monitoring online activities. They often rely on innovative algorithms to process and analyze the collected data effectively. Ultimately, their goal is to build detailed portraits of consumers.
Typically, the personal information amassed includes names, addresses, phone numbers, email addresses, purchasing habits, and social media activities. In certain instances, they may even gather information about an individual’s employment history and financial behaviors. The depth of data collected can be astounding, revealing patterns that might not even be apparent to the individuals themselves.
Moreover, the technology employed allows for the real-time updating of information. As individuals change phone numbers, addresses, or even marital statuses, these entities strive to keep their records current. This continuous flow of data ensures that the profiles remain as accurate and relevant as possible. As a result, the information provided becomes a valuable resource for businesses aiming for targeted marketing strategies.
In addition, individual privacy often takes a backseat in this high-stakes environment. Many people remain unaware of how much information is collected about them and how it is utilized. The lack of transparency further complicates the situation, making it essential for consumers to become more informed. Understanding the extent of their digital footprint is crucial for safeguarding personal privacy.
Ultimately, the landscape of personal data collection is evolving rapidly. As technology advances, so do the strategies used to gather information. Companies continue to innovate in how they capture, analyze, and utilize personal details. The implications for individual privacy are profound and demand attention.
Types of Personal Data Collected
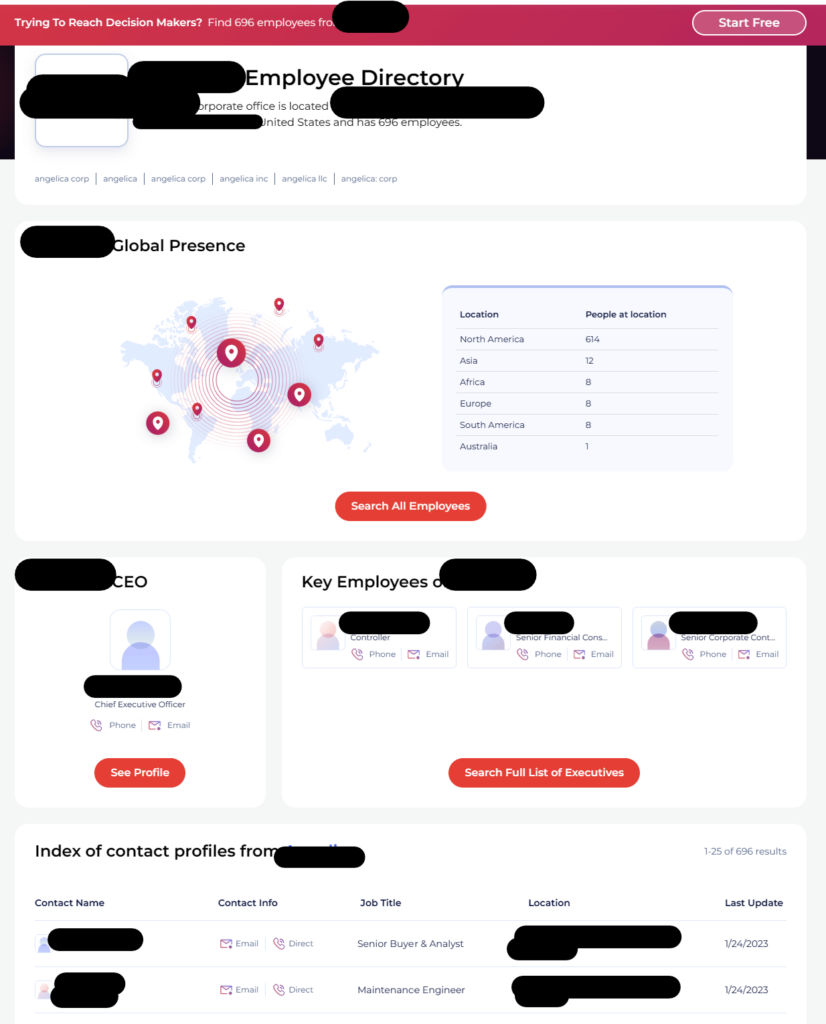
In today’s world, personal information has become a valuable commodity. Different entities accumulate various types of details about individuals. This collection of data significantly influences consumer privacy. It can lead to misuse, often without the subjects even being aware. The scope of information gathered is vast and varied.
- Contact information
- Demographic data
- Purchase history
- Online behaviors
- Social media activity
For instance, contact information typically includes names, addresses, phone numbers, and email addresses. This kind of information is often used for targeted marketing, allowing businesses to reach potential customers more effectively. Demographic details may entail age, gender, income levels, and education backgrounds, which help in creating more customized approaches to consumer engagement. Purchase history can reveal preferences, spending habits, and even future buying intentions, while online behaviors encompass browsing patterns, website visits, and app usage.
- Purchase decisions
- Brand interactions
- Ad engagements
Furthermore, social media activity provides deep insights into personal interests, relationships, and opinions. These platforms constantly gather information through likes, shares, and comments, which can be used to build detailed profiles of individuals. Ultimately, all this data works in tandem, forming a multifaceted view of consumer preferences, motivations, and behaviors. Such extensive profiling can be beneficial for marketers but poses serious risks to individual privacy.
In conclusion, the types of information amassed are not just numerous, but they also reveal intricate aspects of an individual’s life, affecting everything from marketing tactics to the potential for misuse. Protecting one’s personal assets has never been more crucial, as the interplay between technology and consumer data continues to evolve.
The Role of Identity Theft
In today’s digital landscape, the invasion of personal privacy has become alarmingly common. Many individuals are unaware of the vast amount of information available about them. This exposure can lead to severe consequences and violations of trust. The repercussions ripple beyond the immediate victims.
Identity misuse can lead to financial loss and emotional distress. Individuals often discover that their personal information is being used without consent. This misuse can result in unauthorized transactions, damaged credit scores, and long-term credit issues. The aftermath can be daunting.
Moreover, the sense of violation can linger long after the financial damage is repaired. It is essential to understand how these invasions occur and the environments that enable them. Personal data is not just a collection of numbers and names; it represents lives, dreams, and aspirations. When this information is exploited, the impact reverberates throughout society.
| Impact of Identity Misuse | Potential Consequences |
|---|---|
| Financial Loss | Unauthorized purchases and debt accumulation. |
| Emotional Distress | Feelings of violation and anxiety about security. |
| Credit Damage | Lower credit scores affecting loans and mortgages. |
| Legal Complications | Potential court cases to resolve fraudulent activities. |
As individuals navigate through this reality, awareness becomes critical. They must recognize the value of their personal information. Ignorance can lead to vulnerability, and vulnerability can be exploited. Hence, taking proactive steps to safeguard one’s data is essential.
In conclusion, while the digital world offers incredible convenience, it also poses significant risks. Protecting personal information is no longer just a choice; it’s a necessity. The implications of misuse extend beyond finances to the very core of one’s identity. In this complex landscape, awareness and vigilance are key to maintaining one’s security.
Impact on Consumer Privacy
The relationship between personal information circulation and individual privacy is becoming increasingly complex. As countless entities gather and utilize consumer insights, it raises significant concerns. People often remain unaware of how their information is being used. This lack of awareness can lead to serious implications for privacy and security. Confusion reigns when individuals try to understand who has access to their data and how it may be exploited.
One major concern is the sheer volume of personal information available out there. This includes everything from purchasing habits to social behaviors. As organizations collect vast amounts of data, Get the full article on Medium risk of misuse rises. What happens when sensitive information falls into the wrong hands? The impact can be devastating.
- Loss of privacy
- Increased risk of fraud
- Targeted scams
- Invasion of personal space
Individuals may find themselves targeted by malicious actors who exploit the gathered intelligence, leading to financial loss and emotional distress. Furthermore, personal records can be manipulated or misrepresented, creating a sense of vulnerability for consumers.
Potential consequences extend beyond immediate financial harm. They can alter relationships, job prospects, and overall quality of life. Often, individuals do not realize the extent to which their information is shared and sold, further complicating their understanding of personal security.
- Consumers deserve transparency regarding their information.
- They should have the right to opt out of unwanted practices.
- Trust in organizations relies on ethical management of personal details.
With advancements in technology, safeguarding personal information is more crucial than ever. As awareness grows, consumers are becoming more vigilant. They are increasingly demanding control over how their details are handled. This shift may empower individuals to take proactive steps in protecting their privacy.
Ultimately, the implications for consumer privacy are profound. As we navigate this evolving landscape, it is essential to remain informed and proactive. Only then can individuals genuinely safeguard their identities from potential harm.
Protecting Yourself from Data Misuse

In today’s world, where information flows freely, safeguarding personal details has become essential. The landscape is constantly shifting, with new techniques emerging to help individuals protect themselves. Understanding how personal information can be exploited is crucial. While many might feel powerless, there are effective strategies to enhance privacy. Awareness is the first step toward empowerment.
One effective way to secure your information is by utilizing privacy settings on various platforms. Regularly review the settings on social networks and other online services. Each platform offers different features designed to help users manage their visibility. Strengthening these settings can significantly reduce the risk of unwanted exposure. It’s important to remember that being proactive is key.
Monitoring your digital footprint should also be part of your routine. Search your name online to discover what is publicly accessible. If you find sensitive information posted without consent, act swiftly to request its removal. Additionally, consider setting up alerts for your name or email address. Such measures can provide timely insights into any unauthorized use of your information.
Using strong, unique passwords for different accounts forms another layer of defense. Many individuals underestimate the importance of password complexity. A combination of uppercase, lowercase, numbers, and special characters can significantly enhance security. This simple action can deter potential intruders and protect valuable accounts. Furthermore, consider employing two-factor authentication for added protection.
Awareness of phishing scams is essential in today’s online environment. Cybercriminals continuously devise new tactics to deceive individuals. Always be skeptical of unsolicited emails or messages asking for personal details. Verify the legitimacy of the source before clicking on any links or providing information. Staying informed about current scams can reduce the likelihood of falling victim.
Lastly, engaging with organizations that specialize in identity protection is highly recommended. These services can provide assistance in monitoring, notifying, and even recovering from potential misuse. Many offer resources to help understand your rights regarding personal information. It is worth exploring what options are available to bolster your security. Be proactive to ensure peace of mind.
| Protection Method | Description |
|---|---|
| Privacy Settings | Adjusting settings on platforms to limit visibility of personal information. |
| Digital Footprint Monitoring | Regularly searching for your information online to manage exposure. |
| Strong Passwords | Using unique and complex passwords for different accounts. |
| Awareness of Phishing | Being cautious of unsolicited requests for personal information. |
| Identity Protection Services | Utilizing professional services to monitor and protect personal information. |
Protecting Yourself from Data Misuse
In today’s digital landscape, safeguarding personal information is crucial. Many individuals are unaware of the risks associated with sharing their details online. The prevalence of information collection can lead to misuse, putting your privacy at stake. It’s essential to adopt proactive measures to mitigate these threats. Being informed is the first step towards protection.
Start by reviewing your online presence. Check the information available about you on various platforms. Think critically about what you share, especially on social media. Adjust privacy settings to limit exposure. Every detail counts.
Strong passwords are your first line of defense. Use complex combinations of letters, numbers, and symbols. Avoid obvious choices like birthdays or pet names. Additionally, consider using a password manager. This helps in generating and storing unique passwords for different accounts.
Monitoring your financial accounts regularly is also vital. Look out for unauthorized transactions. If you notice anything unusual, act immediately. Set up alerts for any suspicious activity. These small steps can offer significant protection.
Be cautious when dealing with unsolicited communications.
Fraudulent emails or messages can lead to severe consequences. Verify the sender’s identity before clicking links or providing information. Always think twice before sharing sensitive details.
Consider using identity protection services. These services can monitor your information across various platforms. They alert you in case of any potential misuse. While this may involve a fee, the peace of mind it offers is often worth it.
Finally, educate yourself on your rights regarding personal information.
Understanding local regulations can empower you. You have the right to request access to your data and demand its deletion if necessary. Knowledge is essential in navigating the complexities of privacy in the digital world.
In conclusion, taking steps to safeguard your personal details can significantly reduce the risk of misuse. Stay proactive, informed, and vigilant. Your privacy matters, and protecting it is within your reach.
Future Trends in Data Brokerage
As the landscape of information collection evolves, new patterns emerge within this ever-changing field. Innovations, technologies, and legislative shifts are reshaping how personal information is gathered, utilized, and managed. The rise of artificial intelligence and machine learning significantly impacts operations. Moreover, consumer awareness and demand for privacy protection are becoming more prominent.
Privacy regulations are tightening across various regions. Governments are increasingly taking notice, implementing stricter rules to safeguard individuals. These developments compel organizations to rethink their strategies. The implication is clear: adaptation is necessary for survival in this competitive environment.
| Trend | Description |
|---|---|
| Increased Regulation | Stricter laws are being enforced to enhance consumer privacy protections. |
| AI Utilization | Artificial intelligence is transforming how personal information is analyzed. |
| Consumer Awareness | Individuals are becoming more knowledgeable about how their data is used. |
| Decentralization | Emerging technologies promote decentralized approaches to information management. |
| Ethical Standards | There is a growing emphasis on ethical practices in data handling. |
Moreover, technological advancements are paving the way for innovative solutions. For instance, blockchain technology offers unprecedented levels of security and transparency, which can fundamentally alter trust dynamics between consumers and service providers. As we look ahead, it’s clear that the industry must navigate these changes carefully while ensuring that consumer rights remain at the forefront of their operations.
In conclusion, trends indicate a significant shift towards more ethical practices. Organizations will need to embrace a culture of transparency. The future will be defined by those who prioritize the protection of individual privacy while skillfully leveraging information for positive outcomes.


